Archived Webinars
Full Stack Security Assessments | Red/Purple Team Services | Secure Development Lifecycle | Advisory Services
Full Stack Security Assessments
Introduction to Bluetooth Low Energy Exploitation
(Breaking BLE series - part 1)
Bluetooth, especially Bluetooth Low Energy (BLE), has become the ubiquitous backbone that modern devices use to interact with each other. From mobile, to IoT, to automotive, most smart devices now support Bluetooth connections. This enhanced connectivity expands the attacks surface making this attack vector an increasingly necessary aspect of security testing.
| webinar air date: May 28, 2020
Breaking Bluetooth Low Energy - A Deep Dive
(Breaking BLE series - part 2)
Maxine Filcher, Security Consultant at IOActive, will continue from 'Introduction to Bluetooth Low Energy Exploitation,' and present a deep dive into the key components and tools for breaking BLE devices, from the perspective of a pentester and researcher.
| webinar air date: Sept 30, 2020
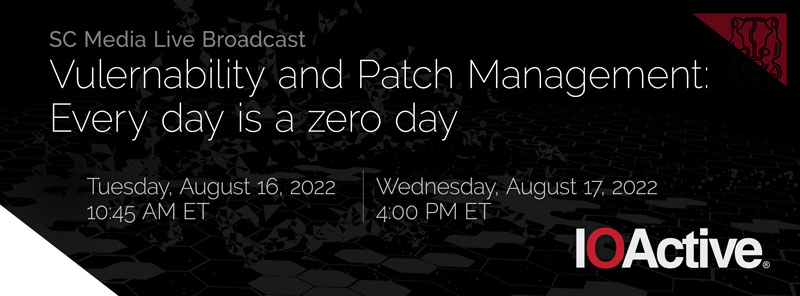
Vulnerability and Patch Management: Every Day is a Zero Day
John Sheehy, SVP of Research and Strategy, participated as a panelist on the SC Media CyberRisk Alliance’s eSummit live broadcast on vulnerability and patch management.
Patch management can be an especially precarious proposition when you’re operating in a work environment where machines and devices must constantly remain operational. Hospitals, factories and power plants are among the many examples of settings where security professionals need to “keep the lights on,” even as they strive to ensure that software and hardware are hardened against the latest vulnerabilities and exploits. The recorded discussion covered the challenges of patching in ICS/OT/IoT environments, and shared strategies for balancing security with operational continuity.
| webcast air date: August 17, 2022
Critical Infrastructure: Hack the Smart City
Modern cities are becoming more connected, making use of new technologies for traffic control, public transport, street lighting, security, and city resource management. This digital transformation to smart systems has a profound impact on cities, helping them operate more efficiently to improve services to residents and businesses, while enhancing citizen well-being, sustainability, and economic development.
This webinar presentation shows you the ever-growing risks of using technology that enables smart cities. With the advancement of information, communication, and IoT technologies, comes new vulnerabilities, and opportunities for cyber attacks, resulting in disruption and denial of services.
| webinar air date: April 25, 2019
Hacking and Securing LoRaWAN Networks
LoRaWAN is becoming the most popular low-power wide-area network (LPWAN) open standard protocol used around the world for Smart Cities, IIoT, Smart Building, etc. LoRaWAN protocol has “built-in encryption” making it “secure by default.” This results in many users blindly trusting LoRaWAN networks without being diligent in assessing security concerns; the implementation issues and weaknesses can make the networks vulnerable to hacking.
Currently, much of the cybersecurity problems of LoRaWAN networks, are not well known. Also, there are no available tools for LoRaWAN network security testing/auditing and attack detection, which makes LoRaWAN deployments a vulnerable target for attackers.
In this webinar, we'll explore the current cybersecurity problems, including the possible attack scenarios, and provide useful techniques on how you can detect them.
| webinar air date: April 22, 2020
Thoughts on Supply Chain Integrity
In this video presentation, John Sheehy, VP, Strategy at IOActive, shares his comprehensive view of the myriad considerations facing businesses as they undertake supply chain integrity assessments, focused on securing operations.
He delves deeply into the pertinent details of: industry definitions of what a supply chain is; potential supply chain disruptions; real-world examples of attacks; various approaches to ensuring supply chain integrity; and thoughts on solutions and what can be done.
| webinar air date: January, 2019
Red and Purple Team Services
Using Red and Purple Team Services to Strengthen Enterprise Security
Red team exercises provide organizations a real-world perspective on the efficacy of their security operations and incident response capabilities. The ability to identify a security incident quickly and respond efficiently is critical to protecting the information and assets most important to your company’s bottom line.
In this webinar, John Sawyer, Director of Services at IOActive, will discuss the collaborative benefits of red and purple teams and how it enhances the ability for enterprise blue teams to fully understand the visibility into each stage of a targeted attack from beginning to end.
| webinar air date: April 9, 2020
Secure Development Lifecycle
Application Security: Security Testing Stock Trading Apps
In this two-part webinar series, security testing stock trading applications will be examined from a fintech application security perspective. Part 1 gives an overview of stock trading platforms technology and risks, and application security testing, and Part 2 provides a deeper dive into the technical aspects of the application security testing methods and discoveries.
Part 1:
Trading Stocks Securely – What You Always Wanted to Know
The days of open outcry on trading floors of the NYSE, NASDAQ, and other stock exchanges around the globe are gone. With the advent of electronic trading platforms and networks, the exchange of financial securities now is easier and faster than ever; but this comes with inherent risks. This webinar will cover
- Why assumptions in security can cause serious issues
- Flaws found in popular trading applications
- Tips for individuals to trade securely
| webinar air date: April 16, 2019
Part 2:
Fintech Security Testing – Uncovering Risks Beyond Trading
In this second and last part of the webinar series on fintech security testing, Alejandro will provide a deeper dive into the technical aspects of the application security testing methods and discoveries. This webinar will:
- Address very basic security testing methodologies
- Use these methodologies to uncover common security deficiencies in applications and assess stock trading technologies
- Show how these financial technologies can be made more secure
| webinar air date: July 17, 2019
Advisory Services
Secure Design and Secure System Architecture Webinar Series
Brook Schoenfield, author, Master Security Architect and former Director of Advisory Services for IOActive, provides deep insights to Secure Design, and Security Systems Architecture concerns.
In this four-part webinar series, Brook will discuss Threat Modeling, DevOps Security, Secure Design and more.
Part 1: An Introduction to Threat Modeling
Threat modeling is the technique to identify attackable design patterns and their solutions. This webinar, This webinar provides an introduction to identifying more secure designs by analyzing which attacks are most likely and the defenses that will mitigate the enumerated attack scenarios.
| webinar air date: June 12, 2019
Part 2: DevOps Security: Oxymoron or Truism?
Many enterprise development teams believe security is too cumbersome for DevOps. At the same time, those charged with application security try for control of the DevOps chain. These positions are based on myths and misunderstandings and lead to unnecessary friction. Security practices benefit from a DevOps mindset, and the automation and code that results. But first, myths must be busted.
| webinar air date: October 2, 2019
Part 3: Secure Design: The Good, the Bad, and the Ugly
Whether you are just starting in secure design, or have a program well underway, this webinar will survey of the benefits that can be reaped from a secure design program, the techniques that will be employed, and solutions to problems that many programs encounter along the way.
| webinar air date: December 5, 2019
Part 4: Secure Design and Systems Architecture -
Bringing it All Together
Secure design remains one of the least understood branches within software security practices. Design practices for security are often ad hoc or performed at the wrong points during development. Software security requires a collection of overlapping, interlocking practices some of which have significant dependencies between each other. Secure design comprises a substantial portion of software security practices. Without these critical design activities, software will lack key security features and may offer attackers exploitable conditions that cannot be corrected by typical security verification tools.
This final installment of the Secure Design webinar series, will pull together the learnings presented in the previous three IOActive secure design webinars, placing secure design into its larger, software security and development context.
| webinar air date: February 19, 2020
To learn more about IOActive security services, please visit: IOActive.com, or contact us directly: ioactive.com/contact/.
Also, be sure to follow us on social media!
©2024 IOActive Inc. All Rights Reserved.
1426 Elliott Avenue W, Seattle, Washington 98119, USA